There are also botnets in the now super-stocked vocabulary of cybercrime. In the last ten years we have witnessed a real surge in cybercrime, thanks to increasingly solid organizations, financially powerful and capable of attacking with ever more sophisticated tools. Viruses such as Wannacry, NotPetya, Stuxnet, DarkHotel, rather than Mirai, have become real stars , infecting millions of computer devices, causing millions of damages, gaining the attention of the general media for the first time, which have proposed their existence to those who probably until then thought that hackers only existed in movies.

Throughout this article, we will focus our attention on Botnets, the deadly networks in which malware viruses, specifically trojans, manage to control millions of computer devices to put them at the service of criminals. Suppose on an individual level a bot may not appear particularly dangerous. In that case, the phenomenon takes on significant proportions when the botnet manages to take control of an enormous number of bots, whose simultaneous action can have devastating effects to say the least, above all because it is conducted without the knowledge of the victims.
So let’s see what a Botnet is, how it is structured and what consequences it can generate once it has reached appreciable numbers in terms of diffusion, in the context of the classic struggle between good and evil, which sees cybercriminal organizations on one side and ‘other police forces and companies in the cyber security sector.
What is a Botnet
The term derives from the combination of the nouns robot and network , in fact a Botnet is a network of robots , computer devices infected by a virus , which connects them remotely to a server capable of controlling them through the internet, to carry out crimes of a computer nature .
Botnets have taken on a negative connotation, but in reality they were not born as tools with bad intentions, but to maintain and manage web services. Today however, as soon as a Botnet is mentioned, the imaginary immediately refers to a network of computers infected with fraudulent purposes.
Botnets do not only involve PCs, but are capable of infecting and manipulating any device that can be controlled via the internet, such as: mobile systems, consoles, IP cameras, smart home devices and the smart devices that we usually subject to IoT systems.
How a botnet is created
Computer devices can be infected in various ways , exploiting a system vulnerability and/or human error. Operating systems and software that are not up to date, as well as incautious clicks on malicious links and attachments are in fact among the most relevant causes of diffusion.
Once a system is infected by a trojan malware, the virus effectively turns it into a zombie by connecting it via the internet with a command & control server through which it is controlled without the knowledge of the rightful owner, anything on the system security devices are not acting in able to detect the threat and successfully eradicate it.
The Botnet therefore acts in an absolutely discreet way, because it must remain as hidden as possible from the attentions of the users of the infected machines, in order to continue to use those devices when it becomes necessary to carry out an IT attack. This is the reason why it is quite difficult to think of having a malicious process active in the background . This action takes place simultaneously on many devices, since the most widespread botnets can even count on the action of millions of infected devices.
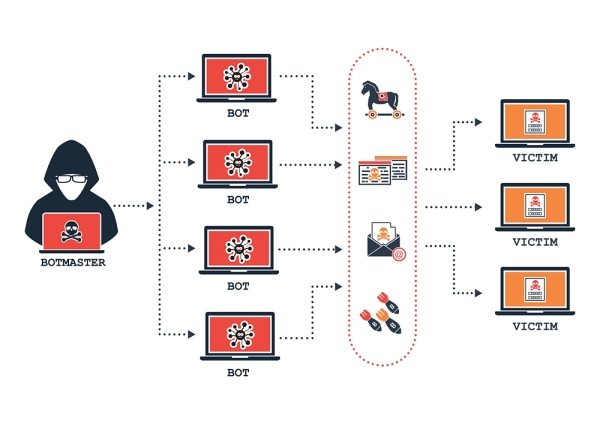
The characteristic elements that make up a Botnet are therefore essentially three:
- The bots : they have the task of spreading the infection, to gain control of an ever-increasing number of devices with which to launch the attacks for which the botnet is set up;
- Botmasters : hackers affiliated with cybercriminal groups who are responsible for programming and managing every functional aspect of the botnet
- The command & control servers : managed by the botmasters, they have the task of connecting with the bots to be able to control them and exchange information of various kinds.
Botnets are characterized by a life cycle consisting of at least four basic stages.
The 4 phases
1. PREPARATION : among the reasons that push cybercriminal groups to invest in Botnets there are essentially economic reasons, as with their activity it is possible to activate many profitable frauds. Other purposes, such as activism and the desire to acquire reputation in dark web environments, cannot be excluded, albeit to a lesser extent. The preparation of a Botnet consists of the programming phases useful for spreading the viral agents called to infect as many devices as possible , in the shortest possible time, and make them bots at the service of a Botnet.
2. INFECTION: to carry out this phase, malware is usually used, through campaigns capable of reaching devices and users with e-mails, text messages, P2P files, links to malicious websites , from which the virus is inexorably downloaded, which subsequently connects with the C&C server and uses the infected device as a bot. The infection takes place exclusively by exploiting the channels present on the Internet. An unconnected device can never be part of a botnet.
3. ACTIVATION: once connected to a C&C server via a background application, the bot receives all the instructions from the botmaster to carry out the operations requested of it, which we will analyze later. The botmaster constantly monitors the devices connected to the Botnet , updating the application that acts as a controller in order to guarantee it the longest possible life, protected from the detection of antivirus or other security systems, which may have been updated in the meantime , finally becoming effective against the threat. Bots can be connected to multiple C&C servers, making the botnet as efficient as possible even if some control servers are taken down.
4. DEATH : the Botnet is characterized by peaks of activity . In fact, a botnet is basically inactive and is put into operation only when the botmaster decides to carry out an attack using his resources. This extremely changeable behavior makes them quite complex to neutralize. Basically, therefore, the botnet always remains active , the bots connected to it vary. This explains why the dynamics of infection are always extremely fast, as they aim to maximize the number of bots in function of imminent attacks. They hardly last more than a few hours and are completely exhausted within a week. Once the intent ceases, the botnet is abandoned for a time, but remains persistent. In fact, it goes without saying that inactivity expresses an apparent death, so much so that often, in addition to devices, even botnets are labeled as zombies, in the particular situation that sees them without access by bots over an entire day.
Botnet architecture
As we have seen, bots have an application running that connects them with C&C servers, through which botmasters are able to control them. The connection between bot and the C&C server takes place essentially according to IT architecture models : centralized and decentralized:
- Botnet with centralized architecture : the bot connects directly to the C&C server to exchange information and receive updates. It is a very simple and quick model to implement, thanks to those qualities which at the same time constitute its objective fragility. If the server is identified and taken down, the botnet essentially dies with it. Attacks conducted through Botnets are usually very fast and aim to maximize their intent within a few hours, knowing that sooner or later they will be neutralized. The bot-server communication always takes place using the internet, via the http protocol of a browser application (pull method, non-continuous connection) or via an IRC chat channel (push method, continuous connection).
- Botnet with decentralized architecture : this is a decidedly more articulated and complex model, which sees a network with nodes in P2P mode in which, in addition to the main C&C servers, the infected devices act both as bots and in turn as servers. The absence of a single central server makes it much more difficult to dismantle a Botnet with these characteristics and the botmasters can work to expand its mesh into the network in an almost unlimited way, even if it is a very complex operation, exclusively within the reach of extremely competent team of hackers.
In addition to the two reference models, there are various forms of hybridization, which are designed by hackers to try to spread the infection faster and more effectively evade security systems, especially firewalls.
The types of attack
Botnets are capable of immense ramifications within the network , reaching the point of infecting and controlling even millions of devices , used to carry out a vast range of fraudulent actions, ranging from direct attacks, to data theft, up to “rental” of the Botnet itself to third parties as “crime as a service” on the dark web . Botnet architects are more often than not real masterminds. So let’s see what are the most common types of attack that their diabolical mind is able to activate by exploiting a Botnet.
Spam Email
Spam campaigns are one of the most common attacks using a botnet, with applications that allow a bot to send more communications per second. This order of magnitude perfectly conveys the idea of the fact that there is a literally impressive amount of spam on the net, which every user who has at least one mailbox receives every day. Fortunately, mail providers have systems capable of filtering spam quite effectively, excluding it from incoming mail. The need to protect users from malicious spam leads providers to close the loops of their security systems, and it is quite frequent that actually reliable emails are filtered, due to some alleged anomalies of the code, rather than due to an insufficiently authoritative sender.
DDoS
DDoS attacks, i.e. Denial of Service , aim to overload a system thanks to a bombing of communications conducted through a Botnet , which has a number of machines such as to put into difficulty the processing capacity of any server, rather than the bandwidth its provision to manage data exchange. This overload prevents a system from working, effectively precluding access to services by its legitimate interlocutors. The nature of the communications sent by bots includes sending UDP packets, rather than TCP or ICMP requests. A famous Botnet used to conduct DDoS attacks was Mirai, still widespread through a series of variants that have taken on its cumbersome legacy, among which we can mention Echbot.
Financial fraud
Some botnets focus specifically on attacks on financial systems, often exploiting endpoint vulnerabilities to steal login credentials or commit other forms of crime . In this case, botnets very often act as loaders for malware specialized in this kind of operation. A very famous case is the Emotet Botnet , to which we will reserve a specific space. A very successful financial malware was Trickbot, also available “as a service”. Its Botnet was recently dismantled by a pool of leading companies in the IT sector, but its “death” could only be apparent and give rise to a series of subvariants.
Information theft
The C&C server can order the malware application installed on the bot to exchange data on that system, or within the network that that machine is connected to. The silent nature of the bot makes it possible to intercept a continuous flow of data , which can naturally contain sensitive data, such as access credentials to protected services, rather than data containing real industrial secrets, which the bad guys can acquire to ask a ransom, rather than trying to sell them to a competitor company, exploiting the dark plots of the dark web.
Advertising fraud
Bots can be used to make automated accesses to certain sites, banners or other ads resources from which to fraudulently obtain a cash reward. In fact, there are many services on the internet that pay for this kind of activity. These are small sums for each click, but a major botnet is capable of making millions of clicks in this way, making the procedure very attractive from an economic point of view. The bots used in this way are called click bots, used to commit what are defined as ad fraud.
Illegal hosting
This practice very often afflicts public administration servers , which are vulnerable due to out-of-date web applications . This is the case of some museum institutions, whose servers have been hacked and connected to a Botnet in order to become repositories for users who are victims of malware to download malicious materials. Since these are poorly maintained servers with very low traffic volumes, it is possible that several days may pass before someone raises the alarm or that the police are able to trace their origin. Recent research has shown that over 90% of public administration sites do not have the most basic security provisions, such as the https protocol. For this reason, many government websites are a gold standard for botmasters.
Malware as a service
As we have mentioned in the case of Botnets for financial fraud, Botnets are often and willingly used to spread malware, which makes it possible to implement real businesses, defined Malware as a Service (MaaS) which provide for the rental of third parties a kit that allows you to activate and manage a finished piece of malware, with basic knowledge to say the least. Do-it-yourself cybercriminals buy a malware kit on the dark web and can try to monetize in no time thanks to information theft and all the malicious practices we have described so far. It is in fact a method that allows you to easily spread ransomware, viruses capable of encrypting data and systems, making them inaccessible to the rightful owner, who is asked for a ransom in order to obtain an unlocking key.
How to protect yourself from a botnet
Contrary to what might be expected, given the frequency with which attacks conducted via a Botnet are successful even in companies of the highest order, protecting themselves from their misdeeds is often simpler than it might seem . The key is in the prudence and general attention of those who use information devices connected to the Internet. Among the main measures that can be taken to avoid being sucked into a Botnet, we can identify:
1) USE OF AN ANTIVIRUS: this is the most basic measure but in itself also the most direct and in itself effective, as it can promptly detect trojans and malware capable of violating the computer device’s operating system and communicate with the background C&C servers. Several basic freemium antiviruses offer these functions in commercial versions, among the premium functions not included in the basic version.
2) OPERATING SYSTEM SECURITY UPDATES : It is good practice to update operating systems and software that may be affected by malware, as developers usually release security patches as soon as news of a vulnerability being exploited by hackers spreads. It is important to pay attention to the zero day attacks of new software releases. As far as IoT devices are concerned, especially those that do not offer particular control interface options, it is generally possible to update the system software by downloading an updated version of the firmware.
3) ATTENTION TO THE SENDER AND THE CONTENT OF E-MAILS: spam emails, with their suspicious links and attachments, are among the most frequent causes of viral infections capable of trapping us in a Botnet. It is therefore good practice to enable the security options of SaaS mail services, rather than the checks provided on local mail clients, capable of blocking suspicious code and attachments. In general, before selecting links and attachments it would be advisable to verify the authenticity of the sender through the properties of the email itself.
4) ATTENTION TO THE LINKS CONTAINED IN THE WEB PAGES: in a similar way to emails, web pages can also download malicious software onto our system capable of connecting us to a Botnet. This almost always occurs by clicking on fraudulent links contained within sites which in many cases appear to be unsuspected.
5) BEWARE OF FILE SHARING SERVICES: many files shared on peer-to-peer networks and downloadable with torrent clients, emule or similar applications, beyond legitimacy, often spread modified versions of the applications, or malicious code in cracks or keygens useful for illegally enabling software: the easiest way to catch a nice trojan.
6) USING A VULNERABILITY SCANNER:if the previous suggestions are to be considered valid in a general sense, and it is desirable that they are used by everyone every time the internet is accessed in any way, the last suggestions are properly related to corporate security systems. The use of software capable of automatically detecting the vulnerabilities of a computer system (vulnerability scanner), are essential to detect those anomalies that could be symptomatic of the presence of malware capable of connecting the hacked devices to a Botnet. Scans should be scheduled regularly, even after any infections have been removed, to ensure that the attacker has not been able to re-enter systems by exploiting secondary vulnerabilities, often triggered by the removed virus.
7) USE OF A HONEYPOT: it is a decoy system, completely similar to the real network, which serves to attract the action of a hacker attack by diverting it from its real target, during the time in which the hacker remains trapped in the honeypot it is possible to study its malevolent behavior in order to implement the appropriate countermeasures on effective systems.
8) USE OF A BEHAVIORAL ANALYSIS SYSTEM:While defending the security perimeter from external attacks is assumed to be at least a best practice for any corporate security team, dealing with the fickleness of internal threats is far more complex to manage. Fortunately, there are software, such as UEBA (User and Entity Behavior Analytics) which allow you to monitor the behavior of authenticated users and devices within a network, to detect any anomalies, which could be an indication of a malicious action caused by a viral agent. These systems should always be integrated with hardware/software IDS (Intrusion Detection System) systems, to ensure a capillary level of protection, especially within the corporate network, where the slightest distraction on the part of an employee can prove fatal.
How to dismantle a botnet: the case of Emotet
If protecting yourself from a botnet is equivalent, as we have seen, to a series of good practices to be implemented on a personal level, rather than in the company, the effort required to dismantle an active botnet on the network is quite different . Such an undertaking goes far beyond the capabilities of a single individual, and requires huge resources, coordinated by international action. To cite an example of large-scale neutralization, we can cite the recent case involving one of the most famous financial Botnets ever: Emotet .
Appearing for the first time in 2014, with the appearance of a trojan, Emotet has subsequently “evolved” as malware, to the point of structuring a planetary Botnet , used to conduct fraud in the financial sector. In its latest evolutions, Emotet has become an Access as a Service, exploited to load other malware , almost all known in the field of financial fraud.
Unlike TrickBot, a very widespread malware, whose Botnet was neutralized by a pool of leading companies in cyber security systems, an international pool of law enforcement agencies belonging to many countries where it was certainly active was implemented against Emotet the botnet . Thus began Operation Ladybird .
After a mistake that led to the arrest of two Ukrainian hackers, the police took possession of some servers used to control the botnet, effectively using it as a honeypot to attract both other criminals and victims of its action. The victims were redirected to automatic disinfection procedures (using a modified version of the malware), while the hackers’ servers were progressively hacked, taken over and subsequently deactivated.
The action, coordinated by Europol, took several months, but effectively dismantled one of the most widespread botnets ever. According to data collected by ENISA (European Union Agency for Cyber Security), Emotet was active in 193 countries, sending over 11 million emails, with a total of nearly 5,000 distribution URLs . A huge network, which seems to have involved over 8 million devices over an activity that lasted several years , which may not have been completely eradicated, since criminals could reactivate the Botnet under other guises, exploiting a variant of it, going to hit precisely those vulnerabilities that have not been resolved in the meantime.
Regardless of what the future holds for us, it would be pointless to sing victories. Botnets will also be a constant in the coming years. The success achieved against Emotet represents in many ways an unprecedented episode, which demonstrated how the communion of intentions and the spirit of collaboration between various nations can counteract the action of cybercriminals, even in the context most congenial to them, where they entrench themselves behind the guise of unsuspecting victims. The direction to be taken is in fact therefore appears to be absolutely collegial in nature.
